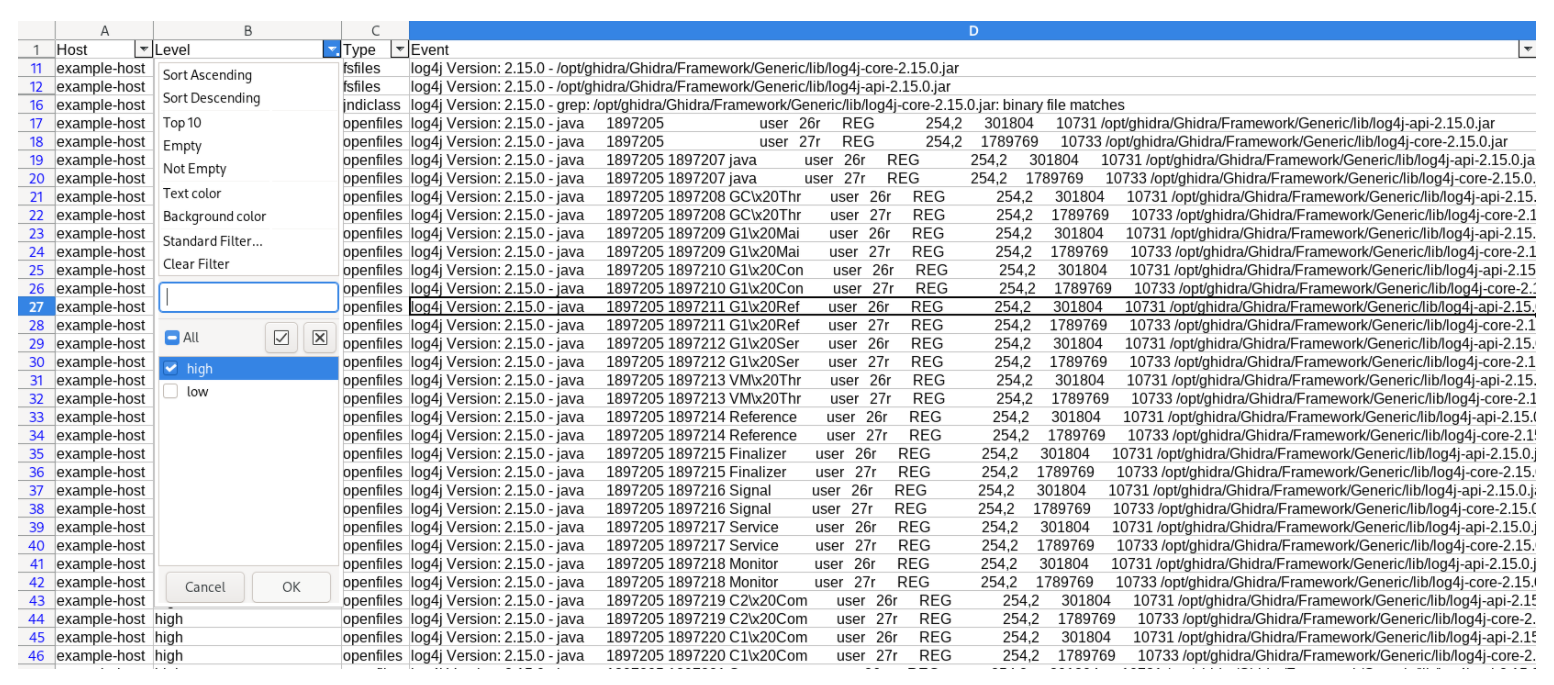
We’ve created two ASGARD playbooks that can help you find Log4j libraries affected by CVE-2021-44228 (log4shell) and CVE-2021-45046 in your environment.
Both playbooks can be found in our public Github repository.
We’ve created a playbook named “log4j-analysis” that helps you find instances that use versions of “log4j”. An additional evaluation script can be used to process the ASGARD playbook results and distinguish between affected and unaffected versions.
Another playbook named “log4shell-detector” allows you to run a script provided by our head of research on all Linux systems to detect exploitation attempts in log files.

The results of the evaluation script that processes the results of the “log4j-analysis” playbook look like this.